🔥
At Only $4.99
Don't leave your cyber security to chance—learn how to protect your digital assets effectively and efficiently. Your data's safety starts with this cyber security checklist!
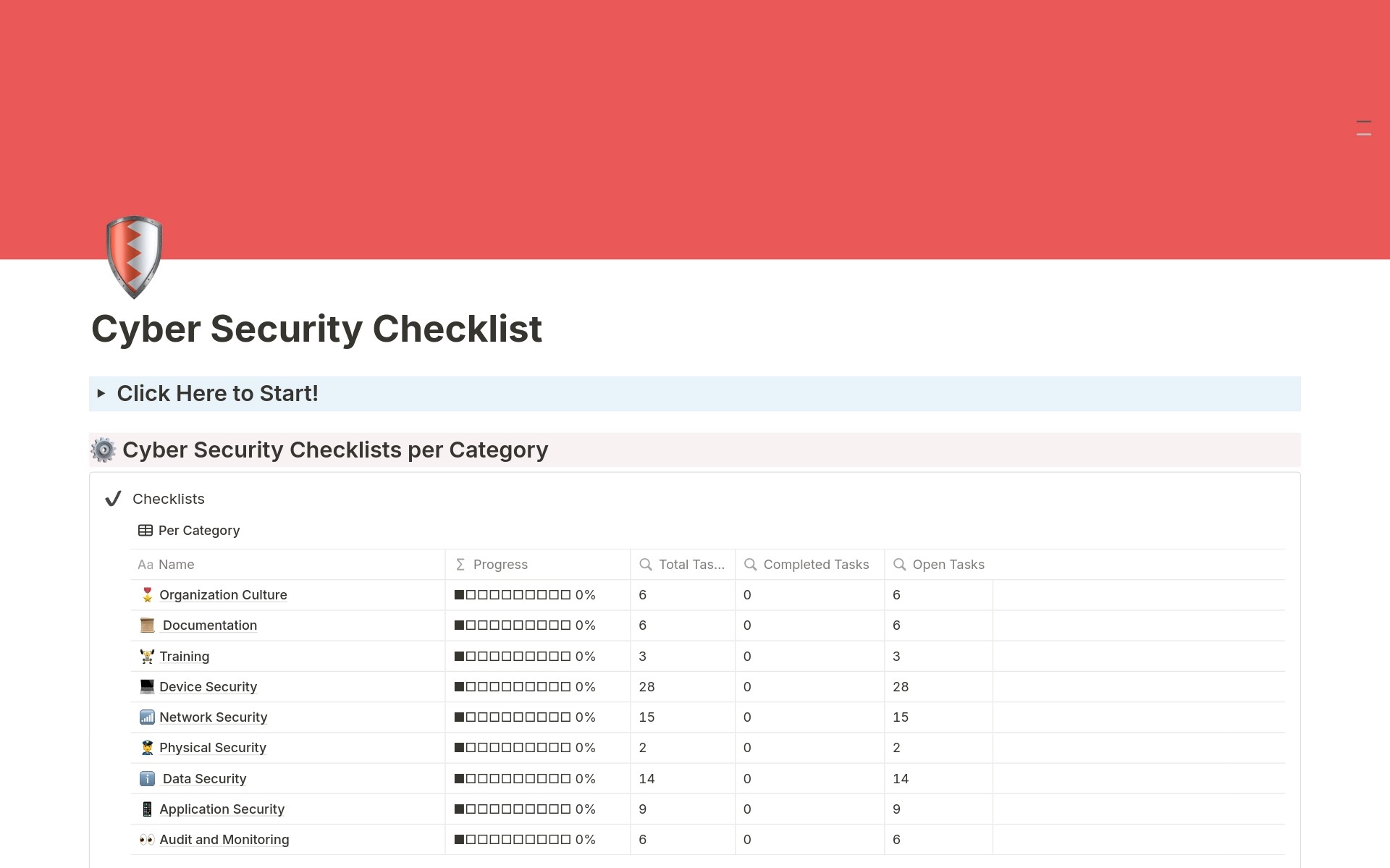
100+ checkpoints under 9 categories
This step-by-step guide covers everything you need to know, from risk management to compliance and incident response.
Hey there! I'm Halil, the creative mind behind this template.
Take control of your online security with this essential cybersecurity checklist.
1M+
Hours Experience
100+
Checkpoints
10
Topics
100+
Social Media Follower
Your ultimate Notion template
This comprehensive guide is your go-to resource for safeguarding sensitive information and preventing costly breaches. Secure your digital world today!
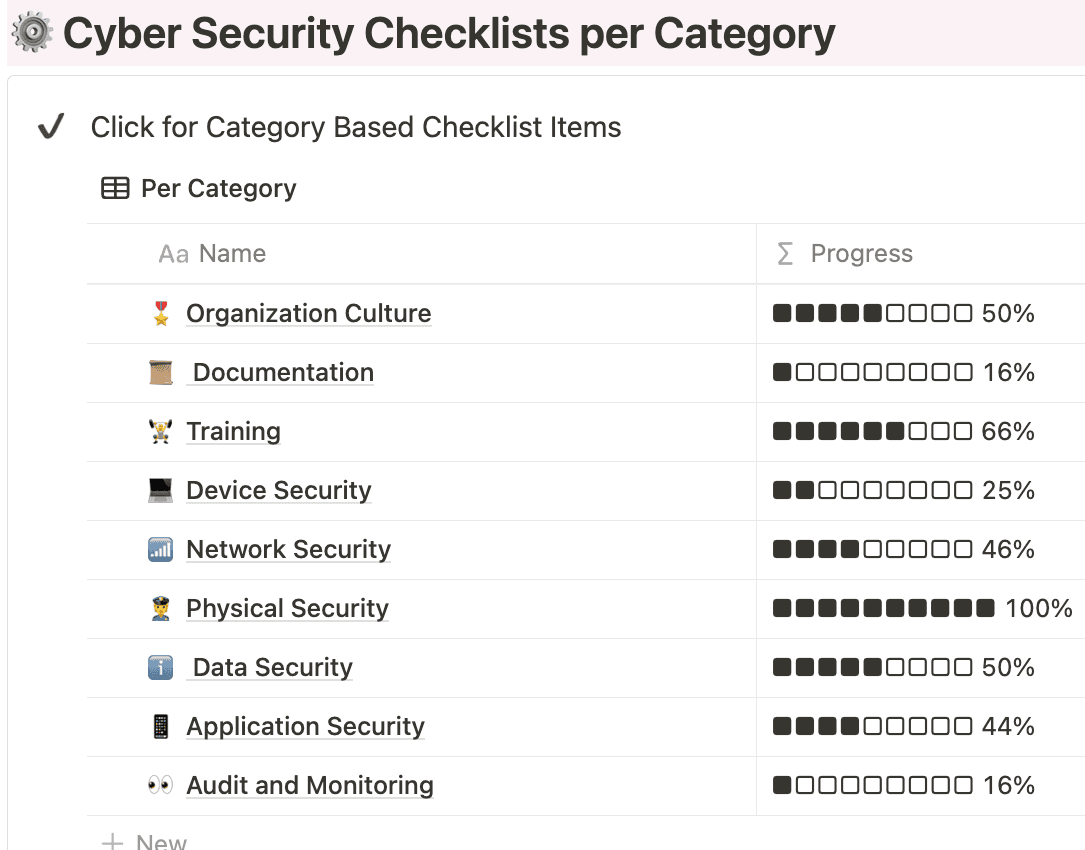
Organization Culture
Building a Security-First Culture: Empowering Your Team to Protect Your Business
Documentation
Essential Documentation: Creating a Clear Path to Cybersecurity Compliance
Training
Essential Cybersecurity Training: Strengthening Your Team's Defenses
Device Security
Keep devices updated with the latest security patches and use strong authentication.
Network Security
Implement robust firewalls and regularly update network configurations.
Physical Security
Ensure secure physical access to prevent unauthorized tampering or theft.
Data Security
Impress stakeholders with professionally crafted reports and presentations.
Application Security
Stay in the loop with real-time updates, ensuring everyone is on the same page.
Audit and Monitoring
Optimize your workflows and save time with efficient and structured templates.
Your guide to Notion template wisdom
Explore the answers to common queries and make the most of your Notion experience.
What is a Cyber Security Checklist?
A cybersecurity checklist is a comprehensive tool designed to help organizations and individuals protect their digital assets from cyber threats. This checklist typically includes a series of tasks, questions, and guidelines that must be followed to ensure that all aspects of cybersecurity are adequately addressed. It covers a wide range of topics, including network security, data protection, user access controls, incident response, and compliance with relevant regulations.
Cybersecurity checklists are not just for IT professionals; they are invaluable for any organization or individual concerned about safeguarding sensitive information and maintaining the integrity of their systems. Whether you run a small business or manage a large corporation, a cybersecurity checklist can serve as a practical guide to help you implement and maintain robust security measures.
Benefits of Using a Cybersecurity Checklist
Comprehensive Risk Management
One of the primary benefits of using a cybersecurity checklist is its role in comprehensive risk management. By systematically addressing various aspects of cybersecurity, the checklist ensures that potential vulnerabilities are identified and mitigated before they can be exploited by malicious actors. This proactive approach helps reduce the likelihood of security breaches and data loss.
Consistency in Security Practices
A cybersecurity checklist promotes consistency in security practices across an organization. It ensures that every team member, regardless of their role or department, follows the same set of security protocols. This uniformity is crucial in minimizing human error, which is often a significant factor in security breaches.
Simplified Compliance
Compliance with industry regulations and standards such as GDPR, HIPAA, and PCI DSS is essential for many organizations. A well-structured cybersecurity checklist can help ensure that all necessary compliance requirements are met. By following the checklist, organizations can systematically address each compliance criterion, reducing the risk of legal penalties and reputational damage.
Enhanced Incident Response
In the event of a cybersecurity incident, a checklist can be a vital tool for incident response. It provides a clear set of steps to follow, ensuring that the response is swift, organized, and effective. This can significantly reduce the impact of the incident and facilitate a quicker recovery.
Resource Optimization
For organizations with limited resources, a cybersecurity checklist can be particularly valuable. It helps prioritize tasks based on their importance and potential impact, ensuring that resources are allocated efficiently. This approach ensures that critical security measures are implemented even when time, budget, or personnel are limited.
Why Use a Cybersecurity Checklist?
Proactive Defense Against Cyber Threats
Cyber threats are constantly evolving, with new vulnerabilities and attack vectors emerging regularly. A cybersecurity checklist serves as a proactive defense mechanism, helping organizations stay ahead of potential threats. By regularly updating and following the checklist, organizations can adapt to new challenges and protect themselves from emerging risks.
Cost-Effective Security Management
Implementing and maintaining cybersecurity measures can be expensive, especially for small and medium-sized enterprises (SMEs). A cybersecurity checklist provides a cost-effective way to manage security by focusing on essential tasks that deliver the most significant impact. This helps organizations avoid unnecessary expenses while still maintaining a high level of security.
Improved Organizational Awareness
A cybersecurity checklist can also serve as an educational tool, raising awareness of cybersecurity issues across the organization. By involving employees in the checklist process, organizations can foster a culture of security-mindedness, encouraging everyone to take responsibility for protecting the organization’s digital assets.
Simplified Audits and Assessments
Regular audits and security assessments are crucial for maintaining a secure environment. A cybersecurity checklist simplifies these processes by providing a clear framework for evaluation. Auditors can use the checklist to verify that all necessary security measures are in place, making the audit process more efficient and less time-consuming.
Foundation for Continuous Improvement
Cybersecurity is not a one-time effort but a continuous process. A cybersecurity checklist provides a solid foundation for ongoing improvement by identifying areas that require regular attention. As new threats emerge and technology evolves, the checklist can be updated to reflect these changes, ensuring that the organization’s security measures remain effective over time.
How to Use a Cybersecurity Checklist
Tailor the Checklist to Your Organization’s Needs
The first step in using a cybersecurity checklist is to tailor it to your organization’s specific needs. Not all organizations face the same risks or have the same security requirements, so it’s essential to customize the checklist to address your unique situation. Consider factors such as the size of your organization, the type of data you handle, and the industry-specific regulations you must comply with.
Assign Responsibilities
Once the checklist is customized, assign responsibilities to the appropriate team members. Each task or section of the checklist should have a designated owner who is accountable for its completion. This ensures that every aspect of cybersecurity is addressed and that nothing falls through the cracks.
Implement and Monitor
After assigning responsibilities, begin implementing the tasks outlined in the checklist. It’s essential to monitor progress regularly to ensure that all tasks are completed on time and that any issues are addressed promptly. Regular monitoring also helps identify areas where additional training or resources may be needed.
Review and Update Regularly
Cybersecurity is a dynamic field, with new threats and technologies emerging all the time. To stay ahead of these changes, it’s crucial to review and update your cybersecurity checklist regularly. Schedule periodic reviews to assess the effectiveness of the checklist and make any necessary adjustments. This will help ensure that your security measures remain relevant and effective.
Conduct Regular Training
A cybersecurity checklist is only effective if the people using it are knowledgeable about cybersecurity best practices. Conduct regular training sessions for your team to ensure that everyone understands the importance of cybersecurity and how to implement the measures outlined in the checklist. Training should be an ongoing process, with updates provided as new threats and technologies arise.
Leverage Technology
Various tools and technologies can help automate and streamline the use of a cybersecurity checklist. For example, project management software can be used to track progress, while cybersecurity software can automate certain tasks, such as vulnerability scanning or patch management. Leveraging these tools can make it easier to manage the checklist and ensure that all tasks are completed efficiently.